认证
RSA认证
签名请求
- 生成你的私钥, 用
appRsaPrivateKey表示, 用于签名请求,长度为2048。 - 构建要签名的字符串
Content_To_Be_Signed. - 使用
SHA256WithRSA加密算法计算并生成签名。 - 将生成的签名添加到请求正文参数
sign中。
有关每个步骤的更多信息,请参阅以下示例。
签名计算步骤
1. 生成密钥对
- 签名使用RSA算法。通信双方生成一组RSA密钥并交换公钥。请求时,私钥用于签名,接收请求的一方使用公钥进行验证。请求则需要按照以下方法生成一套私钥,然后将公钥上传给CodePay.
如果使用Java语言,私钥的格式为PKCS8,而其他语言使用PKCS1。密钥的长度为2048。公钥的格式通常是PEM,一些语言(如C#)需要DER格式的公钥,这些公钥可能需要转换。
- 如果您不知道如何生成RSA2密钥,我们建议您使用以下工具,只需单击一下即可生成密钥、生成签名和验证签名:CodePay Key Tool
- 您也可以使用openssl手动生成RSA2密钥,如下所示:
# 1. Generating the private key
openssl genrsa -out client_private_key_php_dotnet.pem
# 2. If you are a Java developer, convert the private key to PKCS8 format, other development languages use the PKCS1 format
openssl pkcs8 -topk8 -inform PEM -in client_private_key_php_dotnet.pem -outform PEM -nocrypt -out client_private_key_pkcs8.pem
# 3. Generate the public key
openssl rsa -in client_private_key_php_dotnet.pem -pubout -out client_public_key_php_dotnet.pem
# 4. Generate the private key that can be used in Java
cat client_private_key_pkcs8.pem | grep -v "^\-" | tr -d "\n" | sed 's/%$//' > client_private_key_java.pem
# 5. Generate the public key that can be used in Java
cat client_public_key_php_dotnet.pem | grep -v "^\-" | tr -d "\n" | sed 's/%$//' > client_public_key_java.pem
2. 构造要签名的字符串
Step 1: 建立要签名的参数
需要签名的参数包括:API请求参数、响应参数和异步通知参数(但不包括签名参数sign和值为NULL或空字符串的参数)。
根据HTTP协议要求,在GET模式下请求时,如果传递的参数的值中有特殊字符(如:&、@等),则该值需要为URL编码,以便请求的接收方能够接收到正确的参数值。在这种情况下,要签名的数据应该是原始值,而不是编码后的值。例如对接口的调用需要对请求参数电子邮件进行数字签名,那么待签名数据应该是test@msn.com,而不是%40msn.com。
以下参数数组是一个示例:
String [] parameters={
"app_id=wzxxxxxxxxxx",
"method=pay.orderquery",
"format=JSON",
"charset=UTF-8",
"sign_type=RSA2",
"version=1.0",
"timestamp=1908901287917",
"merchant_no=M100001876",
"out_trade_no=TB20181030000875",
"description="
};
处理后需要参与签名的参数为(根据规则,空的ab_no值不参与签名)
String [] parameters={
"app_id=wzxxxxxxxxxx",
"method=pay.orderquery",
"format=JSON",
"charset=UTF-8",
"sign_type=RSA2",
"version=1.0",
"timestamp=1908901287917",
"merchant_no=M100001876",
"out_trade_no=TB20181030000875"
};
由于JSON对象的Key是无序的,因此此签名规则只会选择JSON第一层的Key和Value,对于嵌套的JSON对象,请在签名计算和HTTP消息发送之前将JSON的Value转换为字符串。
{
"key1":"value1",
"key2":"value2",
"key3":{
"subkey31":"subvalue31",
"subkey32":"subvalue32"
}
}
{
"key1":"value1",
"key2":"value2",
"key3":"{\"subkey31\":\"subvalue31\",\"subkey32\":\"subvalue32\"}"
}
Step 2: 参数排序
参数名称ASCII代码从最小到最大排序(从a到z的顺序,如果遇到相同的第一个字母,则查看第二个字母,依此类推)。例如,JAVA语言可以使用函数“Collections.sort(keys)”进行排序。 第一个排序步骤后的数组为:
String[] parameters={
"app_id=wzxxxxxxxxxx",
"charset=UTF-8",
"format=JSON",
"merchant_no=M100001876",
"method=pay.orderquery",
"out_trade_no=TB20181030000875",
"sign_type=RSA2",
"timestamp=1908901287917",
"version=1.0"
};
Step 3: 参数拼接
使用“&”字符连接已排序的参数,如前一示例所示:
app_id=wzxxxxxxxxxx&charset=UTF-8&format=JSON&merchant_no=M100001876&method=pay.orderquery&out_trade_no=TB20181030000875&sign_type=RSA2×tamp=1908901287917&version=1.0
3. 使用签名函数计算签名
使用您所熟悉的开发语言的RSA2签名算法函数对在第二步骤中获得的签名串进行签名。我们使用SHA256WithRSA算法进行签名计算
sign=base64UrlEncode(sha256withrsa(<Content_To_Be_Signed>), <appRsaPrivateKey>));
以下示例可以帮助您验证签名函数计算的结果是否正确:
1. My PKCS8 private key is:MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQCJ9N8YTm0wEuBye5zSiZKncNIg6WBvTHjg4dYc9BH0zR+LeHd/jVo+InrMiIFgblnf7eYJ/wlPG5cSMMSyQMHj/7o0prc+VZsqi1mjX88InK4qDl6qFBFrg4dRrCAwILLVOP/ppUU3souMmnYnvOSUyuLBnhSno8qTpFSbcFAkPaHRmUmcTtVPWuNNbPaZVlNn81imIIVw8LKzOzCz9CNNcikkvbUlZp/cZ0Fl3s6icqOCjRvamg8KLZJs9D52S20X60ynreEIn8g6lr77byOGCCRwpdMl9Cl89WmbC3A3RKh7GRPtjyx3B5aQqE3sK5sNT8H8/EqcnQe8QoVBs7x1AgMBAAECggEAbE6vB+oqlt97DuY1TKVtWb+dePFAIKEtFYC4FKsZndOcvGaripxzCO0Q85sH16lLLh8bxyVPLag/hqx7AGcO0e1nRwbMPkf/NfuJOFZzuBMqOSJm96ghtQLiLiCwdJh3Ticd41U5bmziWlS6BqCp5JcUR2XQWXyiAh+1vQMEKC56CNPxr7imXITS7BYdY0qiGiOANcoEJhfQXn4BjzEm2FJufdlHW6/IeRYZ874HF3/7aUOyhbnapxYHU9PzicMc9XwerMcXMGvOfTUnCtRVONLn7jiknbpwdZ1d8PoItUZuaXdAyY6wFHZF+KvyrEoOV0eWRYzPgku2oSMD7IckUQKBgQDy+etogil+3F8S/qW1WiG6l2tLx5cwq3Ak9weN1zOo8A43obtXRxW2b4fDeol8y6LmYaIW9kKmK0qHEx5LoUSH7VN3FigNpFSa6muVJUuY+ob4H3Je+h3PaqbwhVFzjDofuIolPiJZW64LaFPZcxxD9vM2tZ6txLeMUmGftPoVSwKBgQCRWeNxbvTs8U5UknrdDZHUwXUmy5Qg2LUzxDXdbZXgolMh0AgDShcEFvaF+G3OFHj9vovytt0HtEXyC9LEc6w/a08mtGHiAJbjyjrJCHRNrcFflEm1xseIqXQXDj5Tw05XkAnlWN+r0w3Ix45+GrNhMOGfDkVyQeYI5Jsxxt0dPwKBgFJwcWr4HtQoOSnctKSffCovDfycL7QXtukT18BMb/611F0TxtiKCdfoZ4vvm454GUFJhxF7ZIm0zoid9/15LiNgZp1VKynVw878Epx8FvZEql6tbMTE4DBr41BgK46k2WPB3T1do5HmBVthfnGdGM4Gj+bUII6c3BoEKZNieCeZAoGAQ3rx5wXWW/KjpQvkUqAsJhQyqXI2MRGq/n+Hamen/4QdCEOmlLBfAx0OEqCFifljOpquKl7POvZsyrTGg0IYo9DUDGoOT3hqlRKcPBzasf2LGy6jEetZU48oQFPyh7zSsEBE999M6F6xtZdABjerM+IXvVpIz4TcoSBRFMj4es0CgYEAiNCbs2YPKBFpJq9EYsSsx0GwXAItXFAM71TogWs/8InGNq0PYRZTn9Lq6mFEyLkFql1zWQkS7CG3uDPBV+V2G4MbvoZeFgiQmly7uMQJwbEiKjJBsOzkYY2ZhFYLjGUpGer2U82XeEU6F/Vh4FLkVEE2iB3nPpVQs0qPZxfFZvM=
2. My PKCS1 private key is:MIIEowIBAAKCAQEAifTfGE5tMBLgcnuc0omSp3DSIOlgb0x44OHWHPQR9M0fi3h3f41aPiJ6zIiBYG5Z3+3mCf8JTxuXEjDEskDB4/+6NKa3PlWbKotZo1/PCJyuKg5eqhQRa4OHUawgMCCy1Tj/6aVFN7KLjJp2J7zklMriwZ4Up6PKk6RUm3BQJD2h0ZlJnE7VT1rjTWz2mVZTZ/NYpiCFcPCyszsws/QjTXIpJL21JWaf3GdBZd7OonKjgo0b2poPCi2SbPQ+dkttF+tMp63hCJ/IOpa++28jhggkcKXTJfQpfPVpmwtwN0SoexkT7Y8sdweWkKhN7CubDU/B/PxKnJ0HvEKFQbO8dQIDAQABAoIBAGxOrwfqKpbfew7mNUylbVm/nXjxQCChLRWAuBSrGZ3TnLxmq4qccwjtEPObB9epSy4fG8clTy2oP4asewBnDtHtZ0cGzD5H/zX7iThWc7gTKjkiZveoIbUC4i4gsHSYd04nHeNVOW5s4lpUugagqeSXFEdl0Fl8ogIftb0DBCguegjT8a+4plyE0uwWHWNKohojgDXKBCYX0F5+AY8xJthSbn3ZR1uvyHkWGfO+Bxd/+2lDsoW52qcWB1PT84nDHPV8HqzHFzBrzn01JwrUVTjS5+44pJ26cHWdXfD6CLVGbml3QMmOsBR2Rfir8qxKDldHlkWMz4JLtqEjA+yHJFECgYEA8vnraIIpftxfEv6ltVohupdrS8eXMKtwJPcHjdczqPAON6G7V0cVtm+Hw3qJfMui5mGiFvZCpitKhxMeS6FEh+1TdxYoDaRUmuprlSVLmPqG+B9yXvodz2qm8IVRc4w6H7iKJT4iWVuuC2hT2XMcQ/bzNrWercS3jFJhn7T6FUsCgYEAkVnjcW707PFOVJJ63Q2R1MF1JsuUINi1M8Q13W2V4KJTIdAIA0oXBBb2hfhtzhR4/b6L8rbdB7RF8gvSxHOsP2tPJrRh4gCW48o6yQh0Ta3BX5RJtcbHiKl0Fw4+U8NOV5AJ5Vjfq9MNyMeOfhqzYTDhnw5FckHmCOSbMcbdHT8CgYBScHFq+B7UKDkp3LSkn3wqLw38nC+0F7bpE9fATG/+tdRdE8bYignX6GeL75uOeBlBSYcRe2SJtM6Inff9eS4jYGadVSsp1cPO/BKcfBb2RKperWzExOAwa+NQYCuOpNljwd09XaOR5gVbYX5xnRjOBo/m1CCOnNwaBCmTYngnmQKBgEN68ecF1lvyo6UL5FKgLCYUMqlyNjERqv5/h2pnp/+EHQhDppSwXwMdDhKghYn5Yzqaripezzr2bMq0xoNCGKPQ1AxqDk94apUSnDwc2rH9ixsuoxHrWVOPKEBT8oe80rBARPffTOhesbWXQAY3qzPiF71aSM+E3KEgURTI+HrNAoGBAIjQm7NmDygRaSavRGLErMdBsFwCLVxQDO9U6IFrP/CJxjatD2EWU5/S6uphRMi5Bapdc1kJEuwht7gzwVfldhuDG76GXhYIkJpcu7jECcGxIioyQbDs5GGNmYRWC4xlKRnq9lPNl3hFOhf1YeBS5FRBNogd5z6VULNKj2cXxWbz
3. The string to be signed is:123456789
4. The result of calculating the signature using SHA256WithRSA is:F1kKldW4u0xdSzMqehHLtrX6ntK6gjlZ1Nu1IwcCYAvGe+K9/+9VZymbyNjw038ZcxGspnDqcz7+UnqqJ8gBPpMZ4yZb/NdS5TNqruuSooj2jgPk/PlM+uFH97NlMDuUdGVaflujhcaG9irkq48PHQ1+swaELq7mKov7NU155k7bRPWjNzIggxF5Sgh3qcOBpeWVxp/WghRsjfO4O0tRohiOK5pdcAPkj5VlunUgW0/Yv/uC9sV8dodLloUNWG6W0c/pEJnsG48pLLmhag5tzKm7nbHHUrRyLv37+qAuG9S5eZvKUaVbuFwxP2ekSLHRRIQVlBeJbuqfHRQXxzZaJw==
5. My public key is:MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAifTfGE5tMBLgcnuc0omSp3DSIOlgb0x44OHWHPQR9M0fi3h3f41aPiJ6zIiBYG5Z3+3mCf8JTxuXEjDEskDB4/+6NKa3PlWbKotZo1/PCJyuKg5eqhQRa4OHUawgMCCy1Tj/6aVFN7KLjJp2J7zklMriwZ4Up6PKk6RUm3BQJD2h0ZlJnE7VT1rjTWz2mVZTZ/NYpiCFcPCyszsws/QjTXIpJL21JWaf3GdBZd7OonKjgo0b2poPCi2SbPQ+dkttF+tMp63hCJ/IOpa++28jhggkcKXTJfQpfPVpmwtwN0SoexkT7Y8sdweWkKhN7CubDU/B/PxKnJ0HvEKFQbO8dQIDAQAB
6. Signature Verification Result:true
4. 将生成的签名添加到HTTP请求正文参数 sign
处理响应和异步通知
- 获取网关平台的公钥,用
gatewayRsaPublicKey表示,用于验证签名。 - 构造要验证的内容(
content_to_be_Valided)与请求网关API签名时构造要签名的字符串相同,此处不再重复。 - 从响应消息的消息正文或异步通知接收的消息正文中提取签名,参数关键字为
sign。 - 使用您所熟悉的开发语言的本机函数验证签名。
sha256withrsa_verify(base64UrlDecode(<sign>), <Content_To_Be_Validated>, <gatewayRsaPublicKey>)};
示例代码
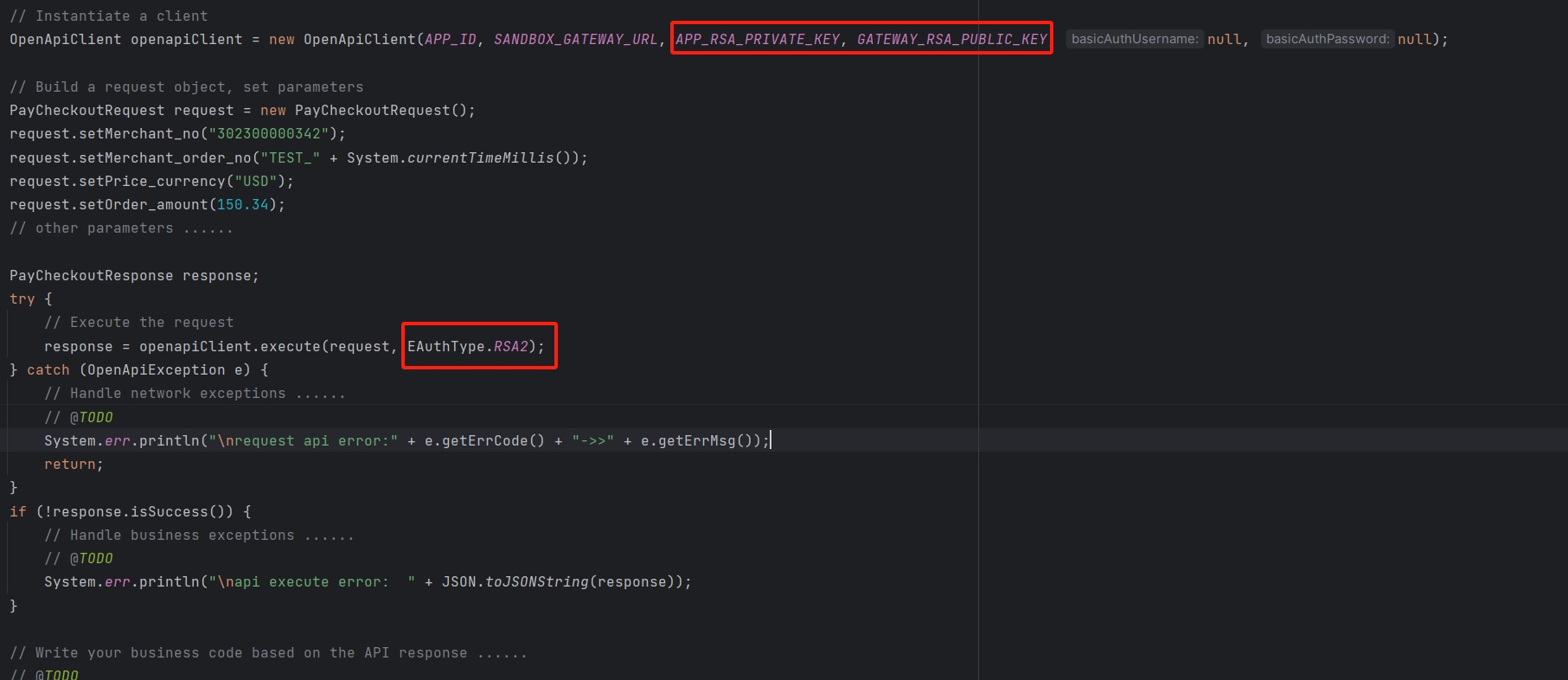
以下是使用Java SDK的示例代码,展示了如何使用RSA进行签名认证,完整的代码请参考 Java SDK:
Basic Auth
Basic Authentication(基本认证)是一种简单的身份验证方式,通常用于HTTP协议中。在这种方式下,客户端在请求头中提供用户名和密码,服务器根据这些信息进行身份验证。
工作原理
- 客户端通过HTTP请求将用户名和密码以特定格式传递给服务器。格式为:
Authorization: Basic <Base64编码的用户名:密码>
其中,<Base64编码的用户名:密码>是将用户名和密码用冒号分隔后进行Base64编码的结果。例如,如果用户名是user,密码是password,那么它们的组合user:password会经过Base64编码成dXNlcjpwYXNzd29yZA==,因此请求头会变成:
Authorization: Basic dXNlcjpwYXNzd29yZA==
- 服务器接收到请求后,会对Authorization头进行解析,解码得到用户名和密码。然后,服务器会检查这些信息是否有效,验证通过后,允许访问请求的资源;否则,返回错误。
示例代码
以下是使用Java SDK的示例代码,展示了如何使用HTTP请求头进行Basic Authentication,完整的代码请参考 Java SDK:
