Encrypting and Decrypting Sensitive Data
Overview
When working with API requests that include sensitive data (like card numbers, CVV, expiration dates, etc.), it’s important to keep the data secure. We use RSA encryption with ECB mode and OAEPPadding to protect this information.
RSA Encryption
Encryption Method
RSA/ECB/OAEPPadding
- RSA: An asymmetric encryption algorithm using a public key to encrypt data and a private key to decrypt it.
- ECB (Electronic Codebook Mode): Encrypts each block of data independently, ideal for fixed-length plaintext blocks.
- OAEPPadding: Adds extra security to RSA encryption and helps prevent certain attacks.
How to Encrypt and Decrypt Data
1. Generate Key Pair
- Create an RSA public and private key pair. The public key encrypts data, and the private key decrypts it. See Generate Key Pair for instructions. Keep your private key secure and upload your public key to the CodePay platform.
- For RSA encryption, you only need CodePay’s public key to encrypt data. You don’t need your own keys unless you want to decrypt sensitive data returned by CodePay. Currently, sensitive data is not returned to developers, so you can skip this step for now.
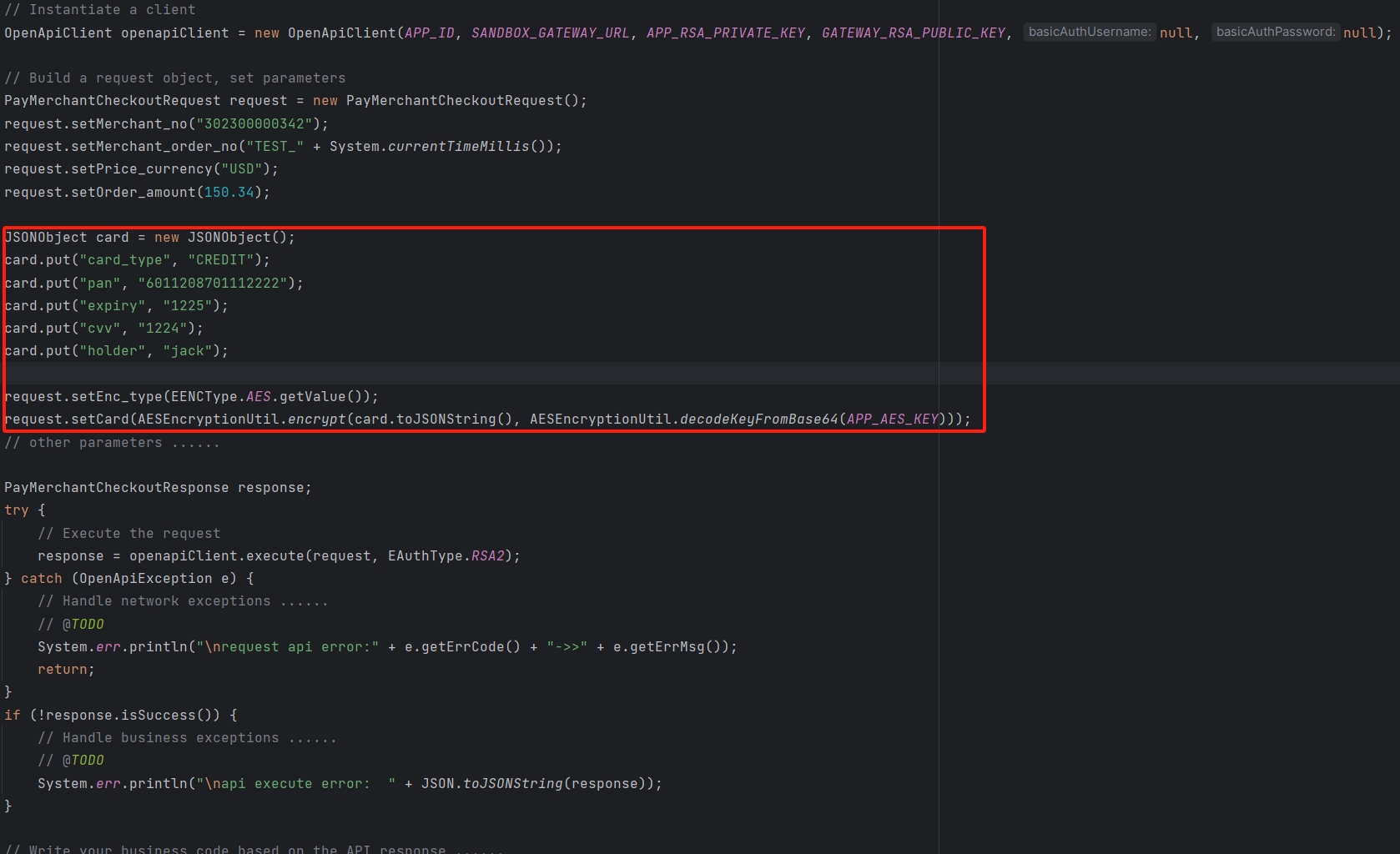
2. Encrypt Sensitive Data
- Use the RSA public key to encrypt sensitive data. When sending requests to CodePay, encrypt the data with CodePay’s public key.
- Make sure to use ECB mode and OAEPPadding during the encryption process.
3. Transmit Encrypted Data
- Convert the encrypted byte array into a Base64 string for easy transmission over the network.
- Send this Base64-encoded data through the API.
4. Decrypt Data
- The recipient decodes the Base64 string and decrypts the data using their RSA private key.
- Make sure to use the same padding scheme (OAEPPadding) during decryption.
When you receive encrypted data in a CodePay response or Webhook notification, use your private key to decrypt it following the same process.
Important Notes
- Key Management: Keep both public and private keys secure. Never share your private key with anyone unauthorized.
- Data Security: Make sure sensitive data stays confidential before encryption, and avoid sending any plaintext over the network.
- Compliance: Follow relevant standards and regulations (e.g., PCI-DSS) when handling sensitive data.
Frequently Asked Questions
- Why does RSA encryption give different results for the same plaintext?
This happens because RSA uses random padding, which is a key feature that makes encryption more secure.
- Random Padding: Each time you encrypt data, the padding algorithm (like OAEP) adds random data before encryption. This means the same plaintext will produce different ciphertext each time.
- Stronger Security: Random padding prevents attackers from guessing patterns and stops repeated plaintexts from always generating the same ciphertext.
- Replay Attack Protection: Because the output is always different, it helps defend against replay attacks.
👉 As long as the data decrypts correctly, the encryption process is working as expected.
References
Sample Code
Here is a sample code using the Java SDK that demonstrates how to use RSA for encryption. For the complete code, please refer to Java SDK:
AES Encryption (Deprecated)
AES (Advanced Encryption Standard) is a symmetric encryption algorithm widely used in data protection. Unlike RSA, AES uses the same key for both encryption and decryption, offering efficient and robust encryption capabilities.
Encryption Algorithm
AES/ECB/PKCS5Padding
AES: A symmetric encryption algorithm that uses a fixed key size (128 bits) to encrypt and decrypt data. AES supports multiple key lengths, including 128, 192, and 256 bits.
ECB (Electronic Codebook Mode): A commonly used encryption mode that splits the input data into fixed-size blocks (typically 128 bits) and encrypts each block independently. While ECB mode is simple in encryption operations, it is vulnerable to certain attacks (e.g., mode analysis attacks) and is not recommended for use in highly sensitive applications.
PKCS5Padding: A padding scheme that ensures the block length matches the algorithm's requirements. If the data block is not long enough, PKCS5Padding will pad it to the appropriate length. PKCS5Padding is suitable for symmetric encryption algorithms to ensure each encrypted block is complete.
Encryption and Decryption Process
Generate Key: Choose an appropriate key length (e.g., 128, 192, or 256 bits). The key generation process should ensure its security to prevent unauthorized access.
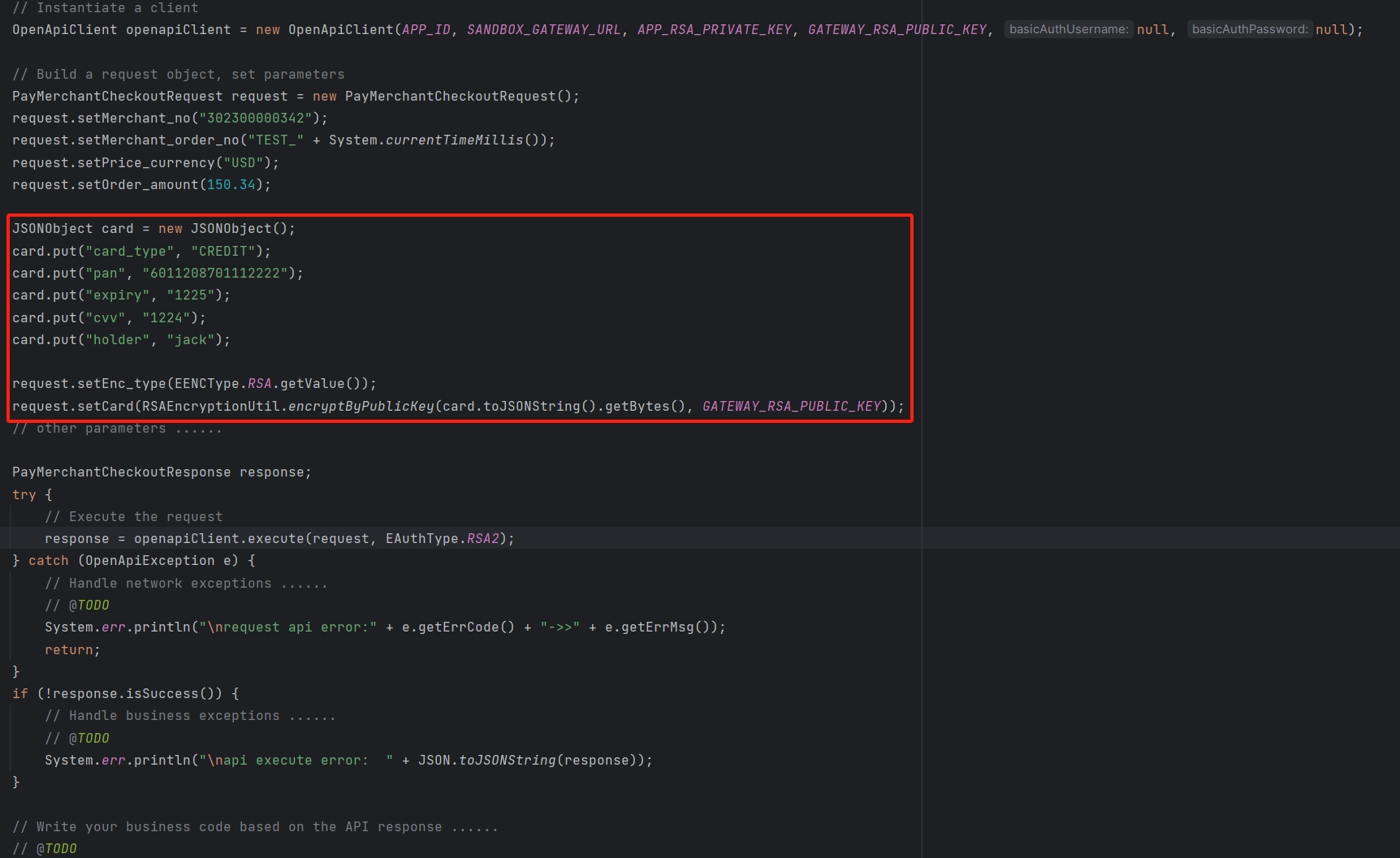
Encrypt Sensitive Data:
- Encrypt sensitive data using the selected key in AES. During encryption, use ECB mode to encrypt each data block independently and apply the PKCS5Padding padding scheme to ensure the data block's length is appropriate.
- Transmit Encrypted Data:
- Encode the encrypted data as a byte array (usually using Base64 encoding) to facilitate transmission over the network. The encoded encrypted data can be returned as part of the API response to the client.
- Decrypt Data:
- The recipient decodes the Base64-encoded data and then decrypts it using the same AES key and padding scheme (PKCS5Padding) to restore the original plaintext data.
Important Notes
- Key Management: Ensure secure storage and management of AES keys to avoid key leakage. A secure key management system should be used to protect the key.
- Padding Scheme: The PKCS5Padding padding scheme is used to fill any gaps in the data block's length, but in some applications, if there are specific length requirements, other padding methods (like PKCS7) may be preferred.
- Limitations of ECB Mode: While ECB mode is simple to use, it is vulnerable to certain attacks because it does not introduce any randomization. In high-security scenarios, other modes (such as CBC mode) are often recommended.
Frequently Asked Questions
Why is the ciphertext different every time with AES encryption? AES encryption, when using certain modes (like CBC), involves randomization. However, ECB mode does not have this feature, so if the ciphertext is the same every time, it could be due to issues with the padding scheme or other encryption parameters. Note that ECB mode always produces the same ciphertext for identical input data, which can lead to security issues, so it is generally advisable to avoid it in certain applications.
How can the security of AES encryption be improved? While AES itself is very secure, using ECB mode may lead to predictable encryption patterns. It is recommended to use more secure encryption modes (like CBC or GCM), along with appropriate randomization strategies (like an IV initialization vector), to enhance encryption security.
References
Sample Code
Here is a sample code using the Java SDK that demonstrates how to use AES for encryption. For the complete code, please refer to Java SDK: